EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USWLAN Security
The support for WLAN security includes all recent options listed here.
The Wi-Fi Alliance developed the Wi-Fi Protected Access (WPA) security suite as one of the original Wi-Fi security suites when they deemed the previous software, Wired Equivalent Privacy (WEP), insecure and weak in algorithm. The Wi-Fi Alliance also developed the cipher suite and temporal key integrity protocol (TKIP) to address the known insecurities of WEP. TKIP used a lengthened key to change and rotate the key more frequently. This was a short-term fix until the Wi-Fi Alliance released the 802.11i standard.
WPA2 (802.11i) then brought about including the cipher suite CCMP and the Advanced Encryption Standard (AES) encryption algorithm. This is considered the de facto Wi-Fi security option by today’s standards.
Wi-Fi Protected Access v3 (WPA3) represents the latest generation in mainstream security for wireless networks. It improves a level of security compared to the widely popular WPA2 standard (released in 2004), yet maintains backward compatibility. However, supporting backward compatibility does not come without its challenges. WPA3 is the future of wireless security moving forward and it's more secure than the current dominant WPA2 standard. WPA3 brings enhanced security and protections for enterprises and end users from the client to the cloud. This brings enhanced security and protections for enterprises and end users from client to cloud.
Three key differentiators for WPA3 are:
- Management Frame Protection (MFP) — The unicast management frames are encrypted, preventing, for example, illegitimate de-authorization of clients (for operating man-in-the-middle attacks, or for intrustion detection system (IDS) and intrusion prevention system (IPS) systems to remove clients. This means that wireless IDS and IPS systems now have less brute-force ways to enforce clients’ policies and will rely more heavily on notifying the system admin about rogue and honeypot APs, for example.
- Simultaneous Authentication of Equals (SAE) — Provides a more secure, password-based authentication and key agreement mechanism even when passwords are not following complexity requirements. It protects from brute-force attacks and makes unwanted decrypting of sessions (during or after the session) much more difficult. Discovering the pass phrase isn’t enough to decrypt the session.
- Transition mode — Personal, Enterprise, and Enhanced Open modes can also operate in Transition Mode. This enables backward compatibility of WPA2 for connecting clients that don’t support WPA3.
WLAN Connection Options
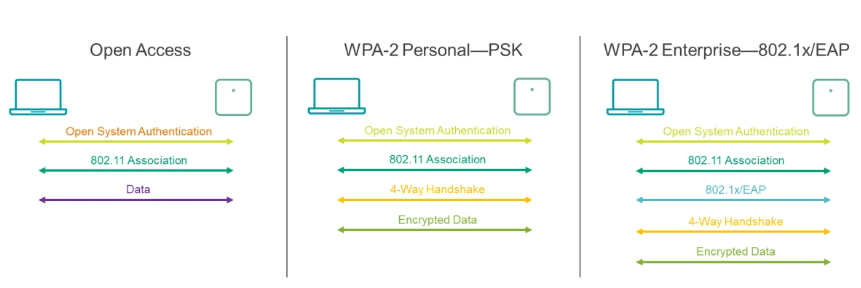
There are two WPA2 options and an open option available to connect to a WLAN:
- Open Access—This option does not include any security and only provides connectivity.
- WPA2-Personal-PSK—The 4-way handshake confirms that the AP and the client have the preshared key (PSK). Once the 4-way handshake completes, the AP and the client establish the keys (key exchange) used to encrypt the data.
- WPA2-Enterprise-802.1x/EAP—This option inserts a credentials exchange to a RADIUS server prior to the 4-Way Handshake. This option is enforced on the AP.
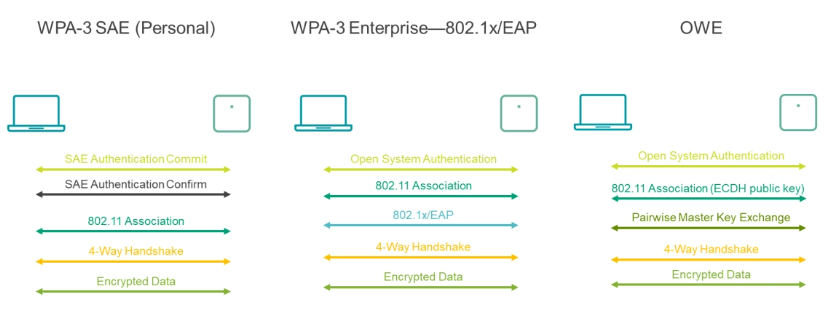
There are three WPA3 options available to connect to a WLAN:
- WPA3 personal (WPA3 SAE)—This is a static passphrase-based method. It surpasses the security provided by WPA2 in cases where a non-complex password is used. The differentiating factor is SAE, the personal authentication process of WPA3.
- WPA3 Enterprise Mode (WPA3 ENT)—Much like its predecessor WPA2 Enterprise, WPA3 ENT is different because it requires MFP. It also includes an optional, stronger 192-bit consistent cryptographic suite for increased security.
- Wi-Fi Enhanced Open Mode—Increases privacy in open networks. It prevents passive eavesdropping by encrypting traffic even when a password is not used, but does not provide security because anyone can still connect to the network.
802.1X/EAP
While 802.1X offers additional security, it also brings with it additional complexity and more “moving parts” such as:
- Supplicant — Refers to the Wi-Fi client in a WLAN
- Authenticator — The device that confirms or denies the authentication attempt
- Authentication Server — The RADIUS server responsible for determining the access (or lack of) for the supplicant
- Directory Service — Provides a repository for any user or device information
The client starts by making a request over the Extensible Authentication Protocol over LAN (EAPoL) protocol. The authenticator then prompts the authenticator server if it identifies whether the client is a trusted client. If the authentication server does not identify the client, it requests a directory server if the client or user is trusted.





LEAVE A COMMENT
Please login here to comment.