EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USWhat is SD-Access ?
Cisco SD-Access Solution is built on principal of Intent based Networking Architecture which help organization to achieve policy-based automation from DC to Branch and from Edge to Cloud.
SD-Access Orchestrate the IT to meet business focus based on On-boarding devices, Fast campus deployment, Secure Segmentation, IoT Integration, and Secure Guest Access.
In this SD-Access or Cisco SDA training you will be able to learn how to implement Intent based Networking Concepts on Branch Network and all the key concepts of SD-Access.
Course Pedagogy
This Cisco SDA training Course Pedagogy will help you to learn the following concepts on Cisco SD-Access.
- What is SD-Access and how it solves the current Network Challenges.
- SD-Access Benefits & Use-cases.
- SD-Access Solution Component Overview
- SD-Access Ordering Guide and Portfolio.
- How to deploy SD-Access fabric and deep-dive traffic Flow
- SD-Access Policy Overview
- SD-Access automation concepts with DNA
- SD-Access Assurance guide
- Design Principal of SD-Access
- How to design Segmentation in SD-Access
- SD-Access Firewall Integration
- How to design Campus Wireless LAN
- How to deploy SD-Access Wireless environment.
Network Challenges without SD-Access:
Following are some challenges that network faces without SD-Access:
Network Deployment:
- Excising Network designs consist of too many network variations, which makes it very hard and challenge to adopt new capabilities and services along with transform to new technology.
- Traditional wireless network are always managed separately and is very difficult to segment.
Service Deployment:
- Any large Layer-2 environment based on VLANs are very much prone to error and cause multiple accident to network due to network loops. Large number of VLANs in any environment is very difficult to manage due to it big Layer 2 boundary.
- Large number of VRF implementation and its segmentation is very difficult to manage and operate makes it complex.
- Traditional method of policy administration (Like ACL building on IP basis) and its Manageability is very complex and often causes issues and network breakdown in network.
User Device & On-boarding
Establishment of user or device based identity along with its implementation of end-to-end policy makes network segment very complex and often causes network breakdown.
Network Operation:
Using outdated Network management Tools causes’ difficulty in maintaining productivity and slow issue resolution.
SD-Access addressing Challenges:
- It automates end-to-end services like segmentation, QOS, and analytics
- It provides user and device policy for any application, it also automates policy across wire and wireless network via single network fabric.
- It allows IT to build and manage network faster and more easily.
SD-Access Benefits:
Automated Deployment across network verticals:
Even though the site is small or very large, SD-Access works and automates network fabric more easily and seamlessly. It also automates inter-site connectivity, branch & campus network and also extends from traditional network architecture to connected workspaces, Operational technology (OT), Manufacturing floors.
SD-Access Integrates Wireless & Wired Infrastructure:
SD-Access Wireless Infrastructure provides following benefits:
- Distributed data Plane: Data plane of SD-Access wireless Infrastructure is distributed at edge switches for optimal performance & Scalability.
- Centralized Wireless Control Plane: Due to Centralized Wireless control plane works both for Client on-boarding as well as Client Mobility.
- Simplified Guest & mobility: With SD-Access Wireless Infrastructure, Anchor WLC is not required any more, and Guest traffic can directly traverse to DMZ without going to foreign controller.
- Policy & Segmentation made Easy: SD-Access makes policy implementation for both Wire and Wireless clients more easily and also segmentation is done end to end in the fabric based on VNI or SGT. It allows IOT ready infrastructure to be segmented across enterprise.
Secure Access to Users & Devices:
SD-access Provide identity based method to define access control policy and network segmentation policy. This automated framework translates the business intent to low level configuration, which is done on devices in network infrastructure.
Correlated Insights & Analytics:
In today traditional environment, issue resolution is very slow, reactive and inefficient, due to distributed & Multivendor environment, fragmented tools, network complexity, and lack of consistence policies.
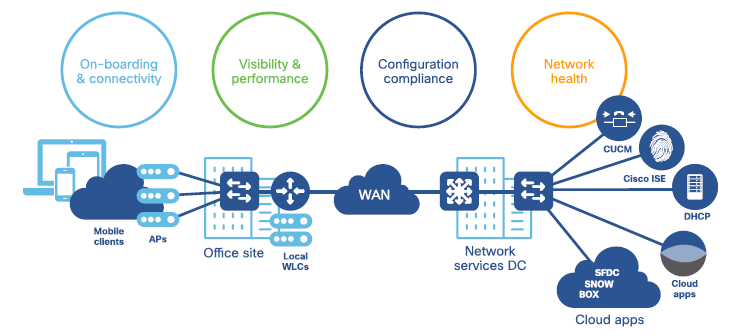
SD-Access collect data from various sources like Syslog, SNMP, netflow, AAA, DHCP, and DNS etc and thus do deep visibility of each flow , and then provides rich actionable insights to optimize network infrastructure for better business decisions.
Note: ( Refer before Purchase )
- We don't offer Any Hands-On labs for practice in this course.
- Lab discussed here contains different Scenarios, task & Its recorded Solutions.
- Content of each page is 30-40% visible for Customer verification about content.
- Before any purchase , verify content then proceed,VLT is in progress,No refund Policy.
- For More Detail : Mail dclessons@dclessons.com , FAQ & TC page.




LEAVE A COMMENT
Please login here to comment.