EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USControl Policy Example 2: Implementing Traffic Engineering
Control Policy Example 2: Implementing Traffic Engineering
-
Problem: Prefer the main data center over the disaster recovery data center. If the main data center fails, traffic should reroute to the DR DC.
-
Solution: Deploy a control policy to influence TLOC priority.
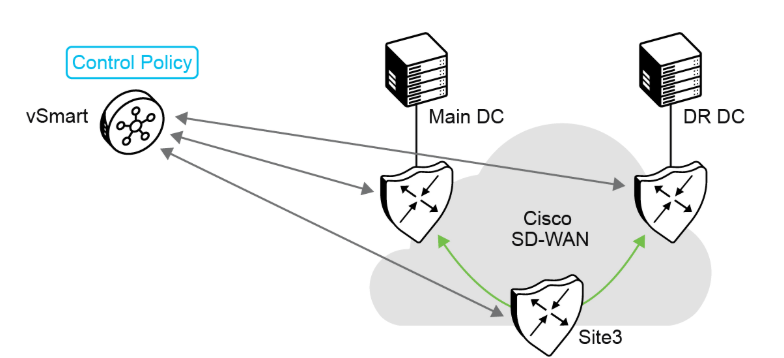
In the example shown in the figure, the goal is to prefer one data center over another. From a routing perspective, a data center is behind one or more TLOCs. The TLOC is the system IP address of the corresponding WAN Edge, plus a color that defines the interface to use. (For simplicity, some details are omitted.)
To prioritize one data center over another, you must give the corresponding TLOCs a higher preference.

Comment
You are will be the first.
TABLE OF CONTENTS
- Onboarding & Provisioning Configuring Templates
- Authentication between vSmart & vBond
- Authentication between vSmart Controller
- Authentication between vBond & vEdge Router
- Authentication between vEdge Router & vManage NMS
- Authentication between vSmart Controller & vEdge Router
- Viptela Specific Port Terminology
- Deploy & Configure vManage & Generate Certificate
- Deploy & Configure vBond & Generate Certificate
- Deploy & Configure vSmart & Generate Certificate
- Configure vEdge & Generate Certificate
- SDWAN & NAT
- Secure DataPlane Bringup
- Enterprise CA for SDWAN Instances
- ZTP Process & PnP Overview
- Control Plane & Data Plane Operation - Unicast Routing Overview
- Configuring OMP & Its attributes
- Configure Unicast Overlay Routing
- Routing Configuration Example
- Segmentation Overview
- Configuring Segmentation
- Segmentation Configuration Example
- Data Traffic across Private WANs
- NAT in SDWAN & Data Encryption
- SD-WAN Viptela Policy Overview
- SD-WAN Centralized & Localized Control Policy Overview
- SD-WAN Centralized & Localized Data Policy
- Service Chaining
- Traffic Flow Monitoring
- vEdge Router as NAT Device
- Zone Based Firewalls
- Configure Centralized Control Policy
- Configuring Centralized Data Policy
- Configuring Cflowd Traffic Monitoring
- Configuring Zone based Firewall
- Service Chaining Configuration Example
- Configuring Service Side NAT
- Configuring Transport side NAT
- Control Policy Example 1: Hierarchical Topology
- Multi-Region Fabric
- Control Policy Example 2: Implementing Traffic Engineering
- Control Policy Example 2: Dynamic On-Demand Tunnels
- LAB Deploy Cisco SD-WAN Edge Routers
- LAB Deploy SDWAN Controllers
- LAB Deploy Cisco SD-WAN Devices Using Configuration Group
- LAB Implement Service-Side Routing Protocols
- LAB Implement TLOC Extensions
- LAB Implement Control Policies
- LAB Implement Data Policies
- LAB Implement Application-Aware Routing
- LAB Implement Branch and Regional Internet Breakouts
- LAB Migrate Branch Sites
RECENT POSTS
- Designing Enterprise-Class Hybrid Cloud Connectivity Using AWS Networking Services
- Exploring Core AWS Networking and Messaging Concepts for Modern Cloud Architectures
- Understanding Key AWS Services for Modern Cloud Architectures
- Building a Strong AWS Foundation with Amazon S3, EC2, and Virtual Private Cloud
- Understanding the ENSDWI Course: Advanced Cisco SD-WAN (Viptela) Concepts
- A Complete Guide to the DCACI-A Course: Mastering Advanced Cisco ACI Concepts
- How Our Online Python Certification Will Prepare You for a Career in Network Automation
- What You'll Learn in Juniper Mist Labs: A Deep Dive into AI-Driven Wireless Networking
- 10 Benefits of Studying Cisco ISE for Network and Security Folks
- Which AWS Advanced Networking Labs Course Includes # Real World Traffic Flows and Examines Objectives?




LEAVE A COMMENT
Please login here to comment.