EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USUmbrella Secure Web Gateway
Cisco Umbrella secure web gateway can proxy all online traffic for enhanced visibility and management, log every activity, defend from viruses and malware, and enforce acceptable usage regulations.
Cisco Umbrella supports IPSec tunnels, AnyConnect clients, PAC files, and proxy chaining. You can use the secure web gateway to inspect and control your traffic to meet regulatory requirements and internal acceptable usage policies.
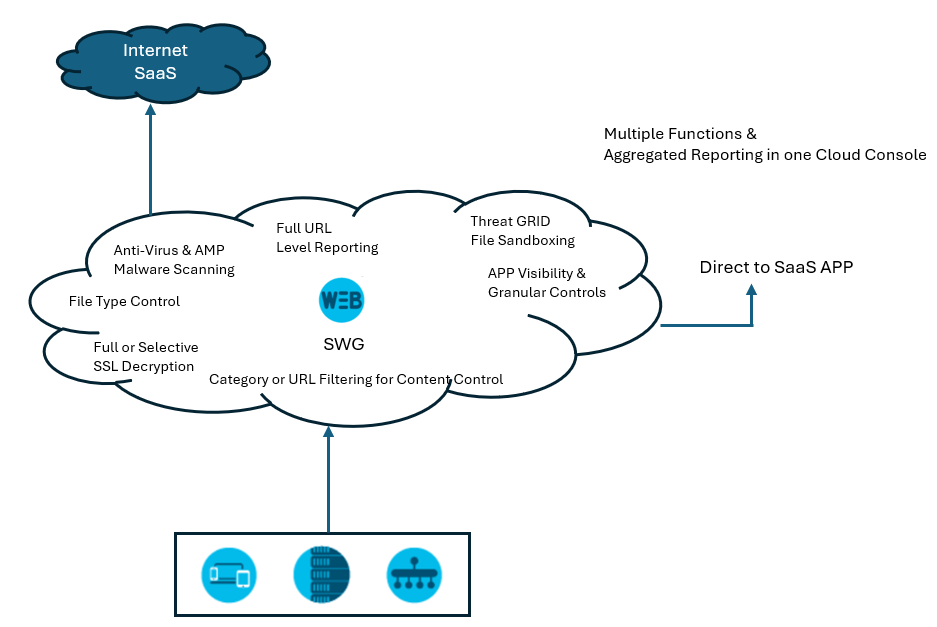
Cisco Umbrella secure web gateway provides a comprehensive set of features that you can configure and manage from a single user-friendly cloud console.
These features are:
URL level logging and reporting:
The Cisco Umbrella console contains comprehensive logging reports that include the complete URL address, network identity, allow or block action, and external IP address. You can filter events by protocol (HTTP or HTTPS), type of event, identity type, and security category. Web content filtering is also available at the URL level to prevent users from accessing specified destinations.
SSL traffic decryption and inspection:
Cisco Umbrella can decrypt and inspect all, or a subset of SSL encrypted traffic.
Application Visibility and Control:
Enabling the detection and reporting of cloud apps in operation across your environment. Cisco Umbrella generates summary data on the vendor, category, application, and volume of activity for each found app automatically. The drill-down reports include risk-related data (for example, the online reputation score, financial sustainability, and any applicable compliance certifications). This information provides more effective cloud adoption management, risk mitigation, and the ability to prevent the usage of offensive or unsuitable cloud applications in the workplace.
Advanced antivirus and anti-malware protection:
Talos threat intelligence powers Cisco Umbrella, which inspects approximately 1.5 million unique malware samples per day.
Sandboxing:
Any new or suspect file types that pass the core malware inspection are transferred to the Sandbox, where they are analyzed for evasive threats, such as time-delayed malware. Administrators receive retrospective alerts when initially assumed to be clean files begin to exhibit malicious activity.
Microsoft 365 direct internet connection:
Cisco Umbrella dynamically detects Microsoft 365 traffic via a Microsoft API. This detection enables Cisco Umbrella to quickly identify essential domains, URLs, and IP addresses for the functioning of Microsoft 365. When Microsoft 365 direct access is enabled on a Cisco Umbrella instance, the necessary traffic is routed directly to the closest Microsoft location via Umbrella's peering arrangements, maximizing performance and user satisfaction.
Integration with Cisco SD-WAN and AnyConnect:
Cisco Umbrella integrates with Cisco SD-WAN and Meraki to facilitate web traffic redirection to the cloud. The secure web gateway integrates with the Cisco AnyConnect client on the network and off-network devices.
Automated tunnel functions:
Normally, you must set up a primary and backup tunnel for each location, adding to the deployment time. In this situation, if the primary data center fails, the administrator must use the console to shift traffic to the backup tunnel. With Cisco Umbrella's Anycast-related patent-pending technology, automated tunnel failover is possible, and does not require a manual intervention to switch tunnels and data centers.
Web Policy Precedence
A Web policy consists of rulesets in which you can store identities and rules and also specify security settings. You can build an unlimited number of rulesets and rules that fit your system's network entities, users, and groups.
Web Policy Rulesets
A Web policy ruleset consists of identifiers and rules. It can include all (for example, individuals from a specific geographic area, business location, or group of networks, users, roaming PCs, and so on). By matching an identity with the requested web address, it chooses a ruleset from your list.
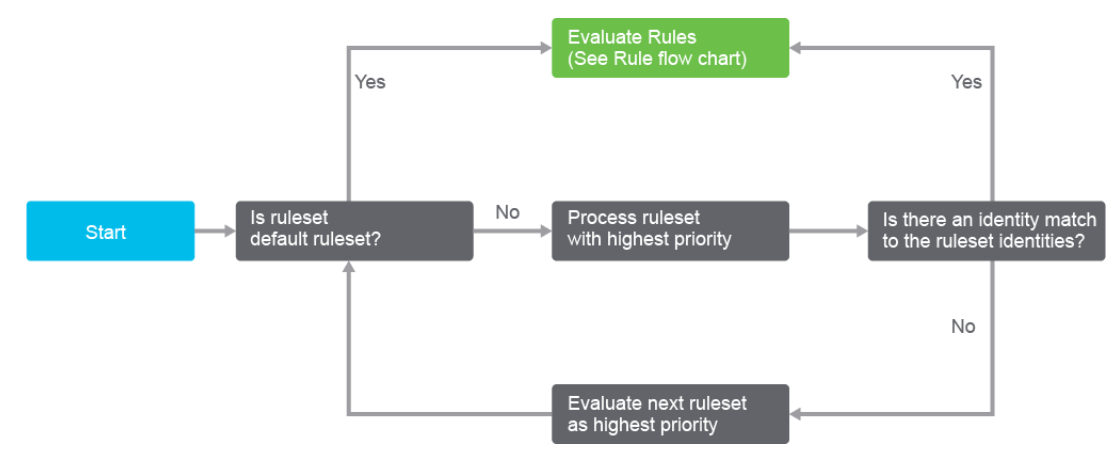
Within a Web policy ruleset, these security settings can be configured:
- Block Page
- File Analysis
- File Type Control
- HTTPS Inspection
- PAC File
- Security Assertion Markup Language (SAML)
- Security categories
- Tenant Controls
- Ruleset logging
Set Up Rulesets
You can prioritize a ruleset after adding it to your Web policy ruleset list. Group your rulesets by priority. Cisco Umbrella arranges the list of rulesets in descending order. If a matching identity is not found in any of your rulesets, Cisco Umbrella uses the Default Web policy ruleset.
Match an Identity to a Ruleset
When a network entity, user, or group sends traffic, Cisco Umbrella looks up matching IDs in Web policy rulesets. Cisco Umbrella chooses a ruleset that fits at least one of the web traffic IDs.





LEAVE A COMMENT
Please login here to comment.