EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USDNS Layer Security
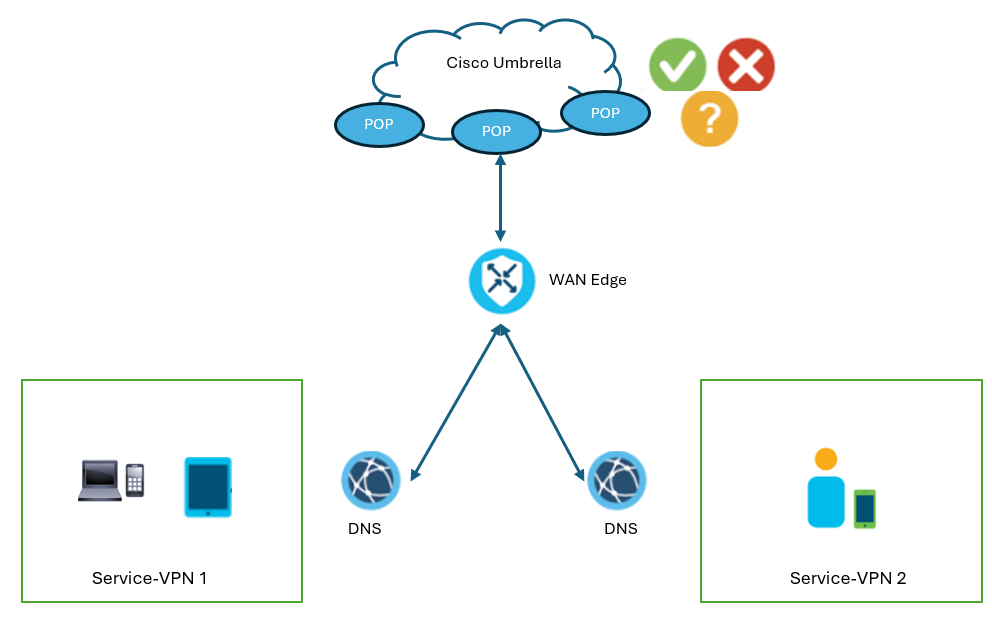
Cisco Umbrella DNS layer security feature integrates into vManage. It enables a network administrator to configure a WAN Edge device to intercept and redirect DNS queries. The WAN edge device forwards the intercepted DNS requests to Cisco Umbrella resolvers or a custom DNS Server. DNS layer security policies apply to one or multiple VPNs.
Configurable DNS Servers
The configurable DNS Servers within the Cisco SD-WAN DNS layer security policy include Cisco Umbrella and Custom DNS Servers.
Cisco Umbrella is a cloud-native platform that unifies firewall, secure web gateway, DNS layer security, Cloud Access Security Broker (CASB), and threat intelligence solutions into a single platform to help businesses secure their network.
The Cisco Umbrella Integration feature enables a cloud-based security service to inspect the DNS queries. The security administrator configures the Cisco Umbrella portal policies to allow or deny traffic towards the fully qualified domain name (FQDN). The WAN Edge device acts as a DNS forwarder, and hence transparently intercepts DNS traffic and forwards the DNS queries to the Cisco Umbrella portal.
Local Domain Bypass
Local domain bypass essentially adds split DNS functionality to DNS layer security. The feature excludes local domains from the policy and does not forward them to Umbrella resolvers or external DNS Servers. The administrator can configure a maximum of 64 local domains under the bypass list, and the allowed domain name length is 100 characters. Some possible regex patterns or formats to enter domain lists on vManage include .*cisco.com, .*.cisco.com.
Cisco Umbrella Connector
The Cisco Umbrella connector intercepts DNS traffic on WAN Edge devices and redirects it to the Cisco Umbrella cloud for security inspection and policy application. The Cisco Umbrella connector redirects type A, quad A (AAAA), and text record (TXT) DNS queries. Other types of queries bypass the connector.
Note
The Cisco Umbrella Connector does not act on HTTP and HTTPS traffic or alter any web traffic.
DNSCrypt
DNSCrypt implements an encryption protocol to authenticate communication between the WAN Edge device and the Cisco Umbrella services. With DNSCrypt, Cisco SD-WAN edge devices download, validate, and parse the peer’s certificate. The Cisco SD-WAN Edge device uses the public key to download the certificate from the Cisco Umbrella DNS services.
Once the Cisco SD-WAN Edge device downloads the certificate, the edge device, and the Umbrella service negotiate a shared secret key and use this secret key to encrypt the DNS queries. The device verifies certificate validity periodically and updates as needed.
Cisco URL Filtering
The Cisco URL Filtering feature enables administrators to provide controlled access to internet or Intranet websites by configuring the URL-based policies and filters. Cisco URL Filtering uses Snort preprocessors to extract the URLs from HTTP and HTTPS traffic (Snort runs in a container). Because Cisco URL Filtering uses the Snort preprocessors, it requires the installation of the Security Virtual Image. The Security Virtual Image is available in the Cisco vManage software repository. Deploying the image requires configuring the device's security policy.
The Cisco URL Filtering policy enforces acceptable use controls to block or allow access based on 82 different categories and web reputation scores. The network administrator can use custom allow and block lists to override category or reputation-based decisions. When the system blocks a specific site according to policy rules, it will notify users. The Cisco URL Filtering solution uses Webroot and BrightCloud databases for URL categorization and reputation.





LEAVE A COMMENT
Please login here to comment.