EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USIntegrating SIG and Cisco SD-WAN
Cisco SD-WAN, routing, security, and other LAN access functions and performance for major companies, can be supplied on high-end devices. On lower-end devices, however, not all security features may be enabled at the same time without compromising performance. These routers can communicate with SIGs, which handle most the processing for enterprise traffic security. When SIG is configured, all client traffic is sent to SIG based on routing or policy. Furthermore, SIG can safeguard roaming users, mobile users, and bring your device (BYOD) scenarios.
Cisco SD-WAN allows automated tunneling to Cisco Umbrella as a SIG in Cisco IOS XE Release 17.2.1r and later. Also, Cisco vManage Release 20.5.1 supports automatic tunneling to Zscaler. Cisco vManage Release 20.4.1 consolidates all SIG workflows into the SIG feature template. This template can be used with both Cisco Umbrella and third-party SIG providers.
DIA traffic entering through the Cisco SD-WAN service VPNs is tunneled to SIGs for enterprise traffic security. All traffic from LAN or WIFI-enabled enterprise clients is routed through SIG.
Network operators have these two options to integrate network devices with SIG:
- Automatic Tunneling
- Manual Tunneling
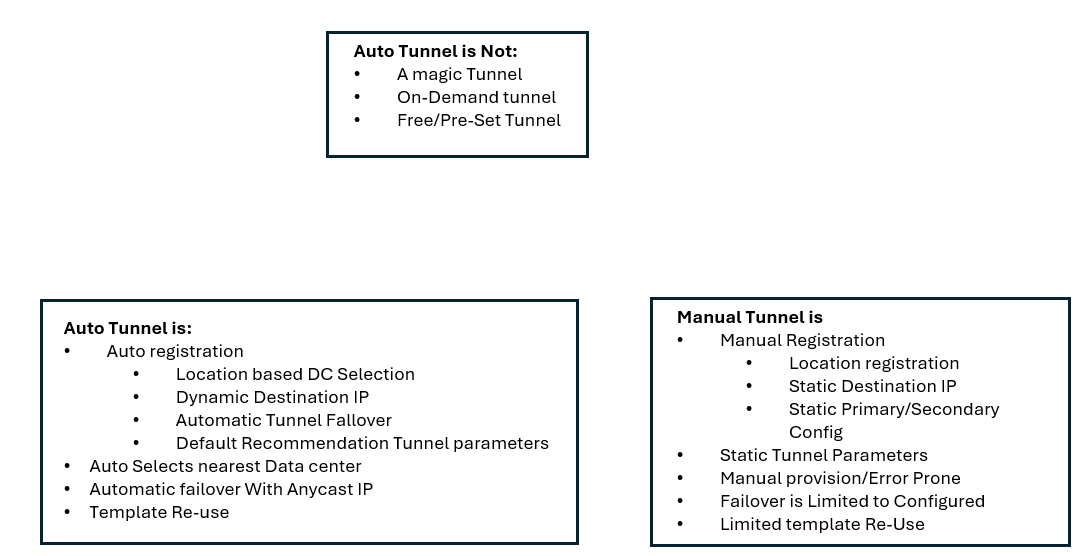
To use automated tunneling, a network operator must complete these steps:
- Complete any prerequisites for SIG.
- Specify the credentials of the SIG by using the SIG Credentials feature template.
- Specify the details for the tunnel to SIG by using the Cisco SIG feature template. In the template, define the parameters for the tunnels, such as the interface name, the source interface, the SIG provider, and so on.
- Edit the Cisco VPN feature template that provides the service route for the devices to the internet.
- Add a service route to the SIG in the Cisco VPN feature template.
- Add feature templates to the device templates of the devices that should route traffic to the SIG.
- Attach the device templates to the devices.
When the device template is attached, the device sets up an IPsec tunnel to the SIG and redirects traffic to it.
Cisco Umbrella:
Use Cisco Umbrella as a SIG by choosing Umbrella as the SIG provider in the Cisco SIG feature template, and then define IPsec tunnels, and tunnel parameters. Use the SIG credentials feature template to specify the Umbrella Organization ID, Registration Key, and Secret.
Zscaler:
In Cisco vManage Release 20.5.1, you can automatically tunnel to Zscaler Internet Access (ZIA) Public Service Edges by using the Cisco SIG feature template. ZIA Public Service Edges are SIGs that can inspect and secure traffic from Cisco SD-WAN devices.
The devices use Zscaler application programming interfaces (APIs) to automatically create tunnels by doing these steps:
- Establish an authenticated session with ZIA.
- Based on the IP address of the device, obtain a list of nearby data centers.
- Provision VPN credentials and location by using ZIA APIs.
- By using the VPN credentials and location, create an IPsec tunnel between the ZIA Public Service Edges and the device.
You can configure a Generic Routing Encapsulation (GRE) or IPsec connection manually by using a SIG template tunnel to support any third-party SIG provider.
Configuring Network Tunnel
To route traffic from an organization's network to Cisco Umbrella, the network operator must configure an IPsec tunnel between the network devices and Umbrella.IPsec tunnels that are established for the CDFW route HTTP and HTTPS traffic on ports 80 and 443 to the Cisco Umbrella secure web gateway.





LEAVE A COMMENT
Please login here to comment.