EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USImplement File Security
Cisco Secure Endpoint
Today's attacks are stealthy and evasive, designed to bypass traditional perimeter defenses like firewalls and IPS. Industry-leading perimeter defense is crucial for any security strategy, but these tools will never be 100 percent effective. Fighting malware effectively today requires new approaches, strategies, and advanced threat capabilities. Malware Defense within Cisco SD-WAN delivers network-based advanced malware protection with security intelligence provided by Cisco Talos and integrated with the Cisco Secure Malware Analytics for advanced file analysis.
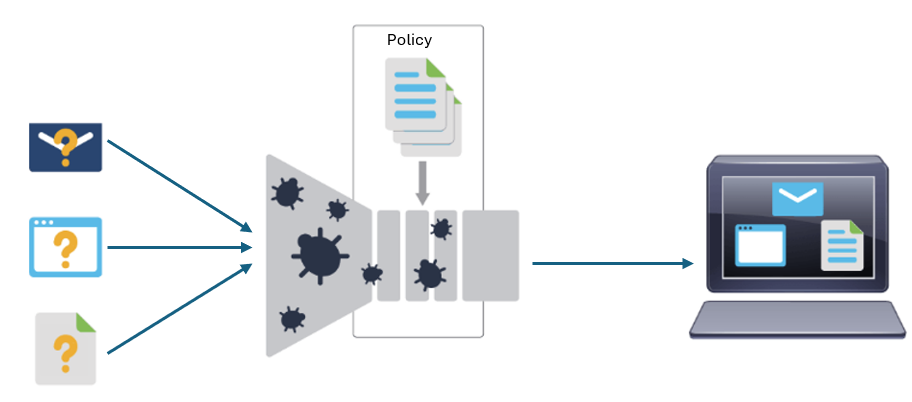
The Cisco Secure Endpoint integration equips routing and Cisco SD-WAN platforms to provide protection and visibility to cover all stages of the malware lifecycle:
- Before: Hardening the network border with firewall rules.
- During: Blocking malware based on File Reputation and IPS Signatures.
- After:
- It uses File Notifications to represent breaches that occurred.
- It is retrospectively detecting malware and providing automatic reporting.
- It uses advanced file analysis capabilities for detection and deeper insight into unknown files in a network.
You can deploy the Cisco Secure Endpoint with Cisco SD-WAN to secure direct internet or cloud access and secure internal communication and stop potential outbreaks and spreading of viruses throughout the network.
Cisco Secure Malware Analytics Overview
Secure Malware Analytics combines advanced sandboxing with threat intelligence into one unified solution to protect organizations from malware. With a robust, context-rich malware knowledge base, it is easy to understand what the malware is doing, attempting to do, how significant a threat it poses, and how to defend against it.
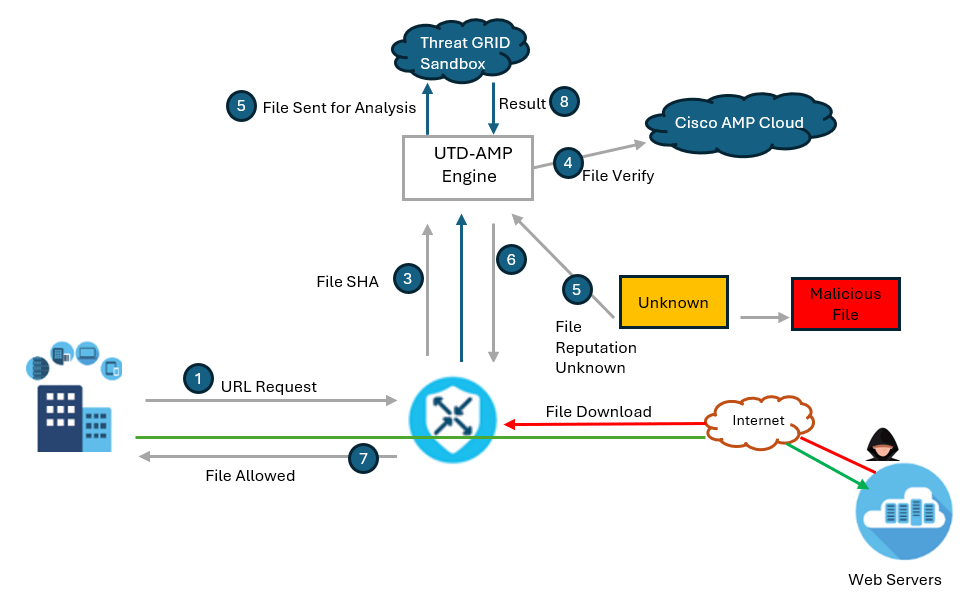
Cisco Secure Malware Analytics provides these features:
- It rapidly analyzes files and suspicious behavior across the organization's network environment.
- It analyzes the behavior of a file against millions of samples and billions of malware artifacts.
- It identifies vital behavioral indicators of malware and its associated campaigns.
- It provides robust search capabilities, correlations, and detailed static and dynamic analyses.
- It provides powerful application programming interfaces (APIs) that integrate and automate existing security products and processes.





LEAVE A COMMENT
Please login here to comment.