EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USCisco SD-WAN Security Types
This topic presents the traditional network and compares it with the evolving business requirements for the network and applications.
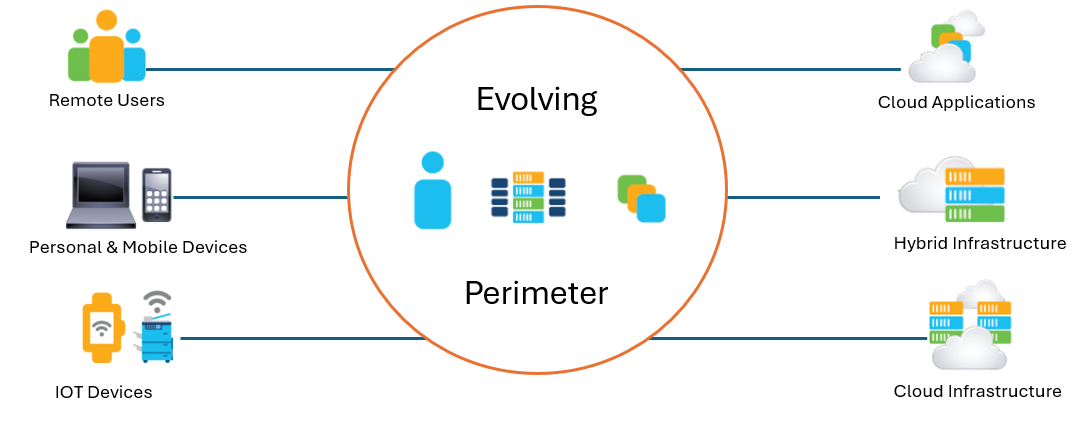
The new IT landscape requires security services to evolve to meet the requirements of the evolving network.
Before looking at the security deployment models and use cases in Cisco SD-WAN, it is important to understand what is driving the evolution of security services and the challenges networks are facing.
In the past, networks were relatively simple. You had local on-premises resources accessed by local users. In addition, you had potential branch users accessing the resources through private connections such as leased lines or Multiprotocol Label Switching (MPLS). Overall, you had a clear perimeter where security services were deployed whether it was the internet edge or the data center.
Today, businesses are using Software as a Service (SaaS) applications hosted in the cloud, and these businesses are migrating their applications to private and/or public clouds, often using multiple cloud providers while still hosting some applications in local data centers.
Users are accessing applications from home or on the road and employees are using their own devices at work.
IoT devices are being deployed in large numbers for smart buildings, worker safety, manufacturing, mining, and shipping use cases.
The number of IoT devices deployed impacts the traditional security perimeter in the sense that it is not easily demarcated anymore. Businesses must now provide access to their resources from anywhere at any time while still enforcing security and compliance requirements.
Design Challenges
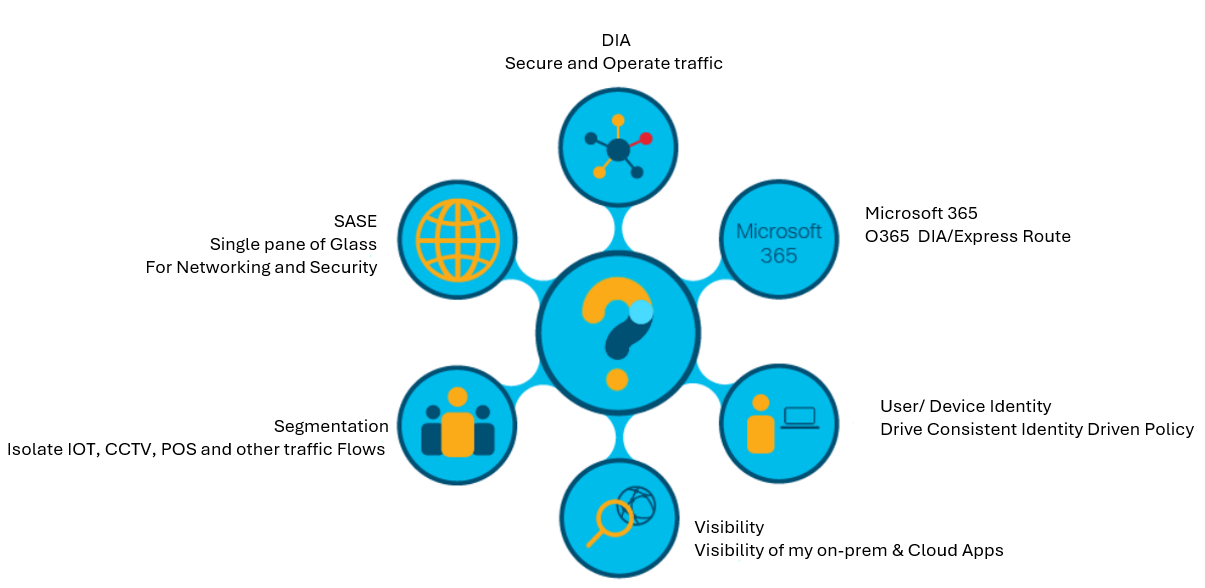
As the network and application landscape has evolved, so have the challenges involved in securing the resources and providing access.
Segmentation Overview
Isolating certain resources may be required for compliance or other regulatory requirements. Implementing segmentation in traditional networks involved configuring virtual LANs (VLANs), VRFs, and access control. As everything was on-premises, this was a simple task. Within the new IT landscape where users and applications are everywhere, it becomes a challenge. Cisco SD-WAN provides end-to-end segmentation across the WAN fabric enabling organizations to deploy different topologies per VPN based on the organization or regulatory requirements.
SASE Overview
With the expansion of home office work or remote teleworkers and the increase of IoT devices, providing secure access to applications from anywhere and at any time is business-critical and brings with it a new set of challenges not present in traditional network designs. The infrastructure must provide access services for local and remote users at any time along with the required security services to secure both network and application access.
DIA Overview
Another change in the way networks are deployed is DIA from remote locations. Traditionally internet traffic was backhauled to a central internet POP where security services were deployed. With DIA, organizations must now secure internet access from each location. This deployment presents a new set of challenges such as how to define and maintain the necessary security policy. Keeping a set of access controls local to a site over multiple sites can be impossible to manage. A single pane of glass to define and manage the security policy is required.
SaaS Overview
Along with DIA, organizations are relying more on SaaS applications, such as Microsoft 365, that are hosted in the cloud. The network must now provide secure low latency connectivity to SaaS applications using DIA, Express Route, or other connectivity options.
Identity Overview
With the dissolution of the traditional perimeter, a consistent and reliable user and device identity is critical. Without proper identity services, it is next to impossible to deploy appropriate policies.
Visibility Overview
And with all the challenges that were mentioned so far, having visibility across the network, and into the cloud infrastructure, as well as visibility across all applications is now even more challenging.




LEAVE A COMMENT
Please login here to comment.