EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USApstra Security Policy
A security policy assists in implementing security in your network. You can use security policies on Layer 2 (L2) IPv4-enabled blueprints but not on IPv6-enabled blueprints. With security policies, you can simplify security management when using multiple vendors. You can also isolate virtual machines and control the permitted application flows between virtual networks. In a nutshell, security policies are used to push access control lists (ACLs) to the top-of-rack switches.
you can deploy many policies and Juniper Apstra will merge them and configure the resulting ACLs on the devices using the vendor-specific syntax. You only need to configure a security policy once, and Juniper Apstra replicates and converts those policies to the CLI syntax of the different vendors and device types in your network.
Objects
The endpoints or groups that can be subject to security policies are:
- Virtual networks (contain subnet)
- Internal IP endpoints associated with virtual networks (contain IP /32 address)
- Internal IP endpoint groups
- External IP endpoints (contain /32 or subnet)
- External IP endpoint groups
- Routing zone (logical collection of all virtual networks and internal IP endpoints)
You can associate one or more security policies with endpoints or groups of endpoints. You can indicate whether you want to log actions taken by specific rules.
Policies
You can apply policies at the Layer 3 (L3) interfaces of the top-of-rack switches (a switch virtual interface [SVI], for example). In the policies, you specify the source address, destination address, protocol, and ports that are to be filtered using an ACLs. The filters applied using security policy are stateless filters.
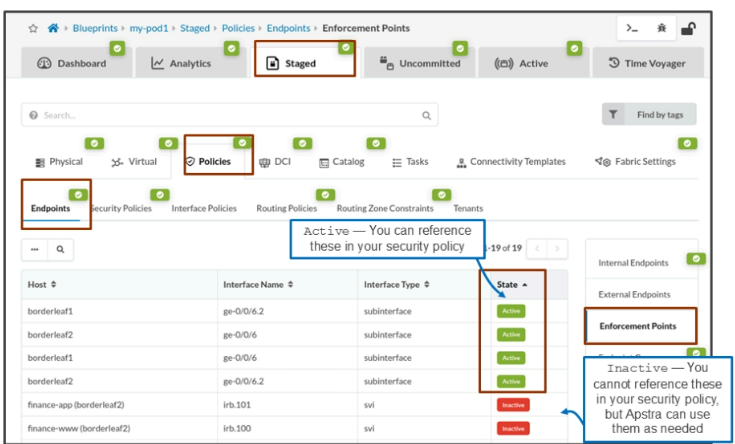
Enforcement Points
Remember, security policies equate to IPv4 access lists. They must apply to an IPv4-addressed interface somewhere in your blueprint. An enforcement point is any IPv4-addressed interface in your blueprint that is not a loopback address or a spine-to-leaf link. An enforcement point is usually an SVI interface that belongs to a VPN routing and forwarding (VRF) table, as part of a routing zone, or an L3 interface that faces a generic system.
The below figure shows that enforcement points can be active or inactive. If it is active, then you can reference it in your security policy. If it is inactive, then you cannot reference it in your security policy. However, in either case, Apstra can use the entire list to apply its ACLs.
Global Security Policy Settings
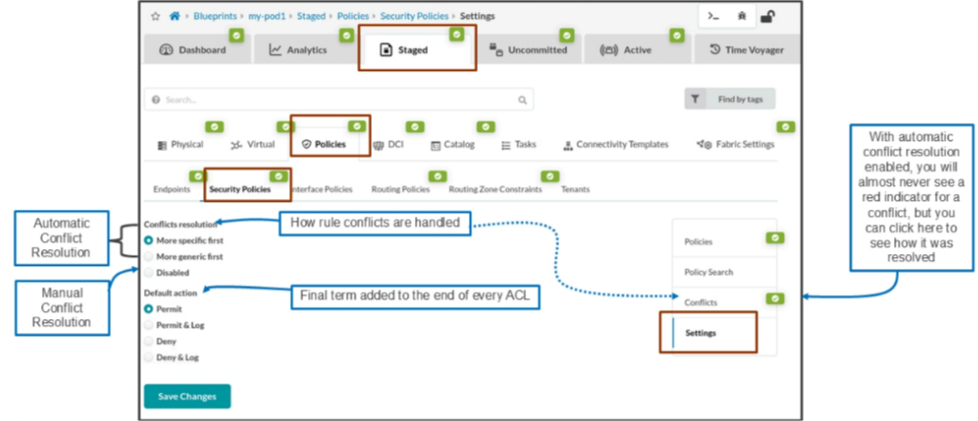
Before creating your first security policy, understand that Apstra has two global settings that get applied to all security policies:
- Conflicts resolution — You can create many security policies and apply them all at once to your blueprint. As your security policies get more complicated, you may accidentally create rules that contradict each other. Apstra automatically detects these conflicting rules. With this setting, Apstra either automatically resolves the conflicts or you must manually resolve the conflicts yourself. We will discuss conflict resolution later in this module.
- Default action — Apstra adds the action selected as the last rule of each security policy. Any changes to these settings will affect both the new and existing security policies, so use them with caution.




LEAVE A COMMENT
Please login here to comment.