EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USACI Object Model Definitation
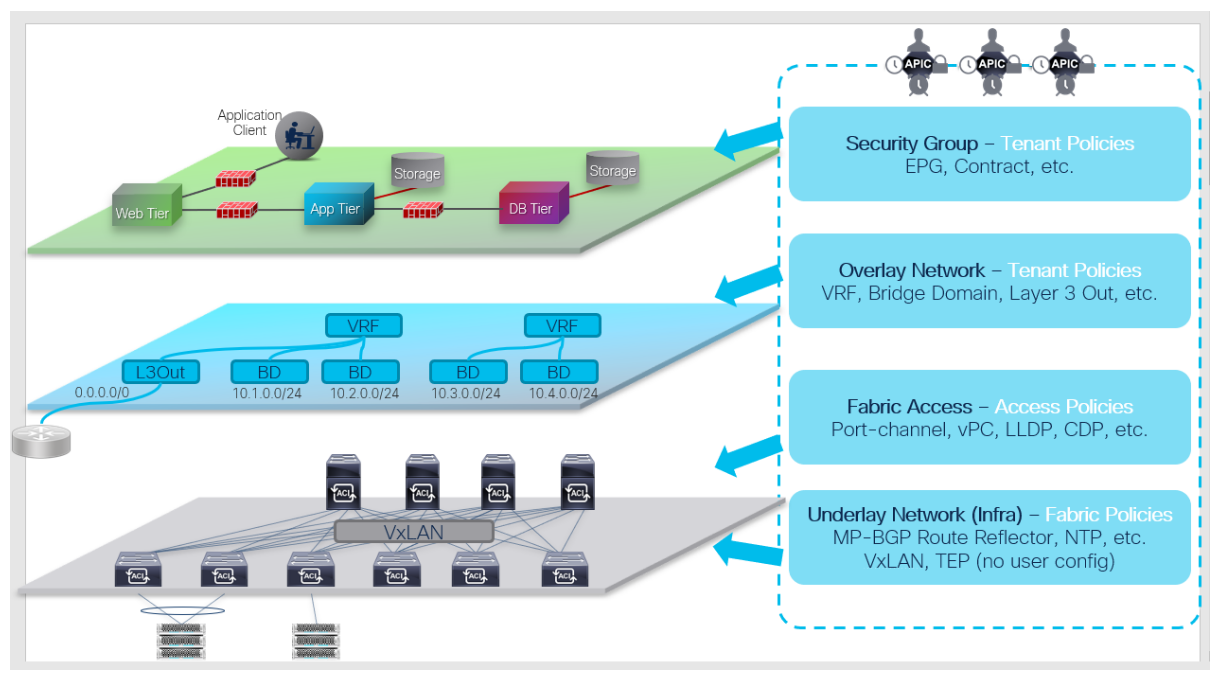
The Cisco ACI manages all the configurations as objects stored in management information tree (MIT) database. As an overview, policies can be categorized in 4 major groups, as shown in the figure below:
-
Security Group (Security/Application Tenant Policies): Defines how ACI fabric should allow network communication between two devices. Example policies are endpoint groups (EPGs), contracts, and so on.
-
Overlay Network (Network Tenant Policies): Defines the overlay network that goes over the ACI fabric. These policies will be the logical topology of user networks and can be defined without worrying about the underlay. Example policies are VRF, bridge domain (BD), and so on.
-
Fabric Access (Access Policies): Defines how end hosts or external network devices are connected to ACI fabric by configuring port-channel, vPC, and other interface-level configurations.
-
Underlay Network (Fabric Policies): Defines the VXLAN underlay built by ACI fabric along with infra Multiprotocol Border Gateway Protocol (MP-BGP) and other protocols to manage ACI switches such as NTP.
In Cisco ACI, all objects are stored in a tree called MIT as mentioned before. And each object is called managed object (MO).
All information including config, hardware component (such as leaf, fan), control plane status (such as OSPF), stats (such as interface stats), and some logs (faults, event, audit log) are stored as an object in MIT that can be easily processed in a programmatic way.
These objects are accessible through REST API and most of the operations in ACI is using the REST API in the background.
Configuration is through REST API (or GUI, NX-OS style CLI that runs API in background). The user configurations are called logical model objects and it’s translated into objects called concrete objects when passed down to switch nodes. Then switch nodes apply the configuration to hardware based on the concrete objects.
Each object is represented by an ID called distinguished name (DN). Each distinguished name belongs to a class which is a type of object.
Methods and Tools to Query the MIT
The MIT can be queried for all objects of a specific class or distinguished name, and then it can retrieve the children or complete subtree for the returned objects.
You can query or view the MIT in different ways:
-
Object Store Browser: https://apic_ip/visore.html or from Cisco APIC GUI
-
Browsing MIT in shell: cd /mit/… or cd /aci
-
Moquery: Direct CLI query to the database
-
REST: Postman, curl GET and POST
-
icurl (local REST client on apic/leaf)
-
Python SDK
These two types of queries are supported:
-
Class-level query: search the MIT for objects of a specific class
-
Object-level query: search the MIT for a specific distinguished name
Object Store Browser
Visore or Object Store Browser is a utility that is built into Cisco APIC and allows a user to easily browse MOs using an HTML browser.
The Object Store Browser utility uses the Cisco APIC XML API query methods to browse the MOs that are active in the Cisco APIC. You cannot use the Object Store Browser utility to perform configuration operations.
The core principles of Object Store Browser are as follows:
-
Managed Object browser in GUI
-
Can be accessed in various ways:
-
From Help and tools icon in APIC GUI.
-
Right-click on any ACI object in the GUI.
-
By connecting to https://apic_ip/visore.html
-
-
Used to retrieve:
-
All object of certain class
-
Certain DN object
-
Review object properties
-
Relations to parent and children objects
-
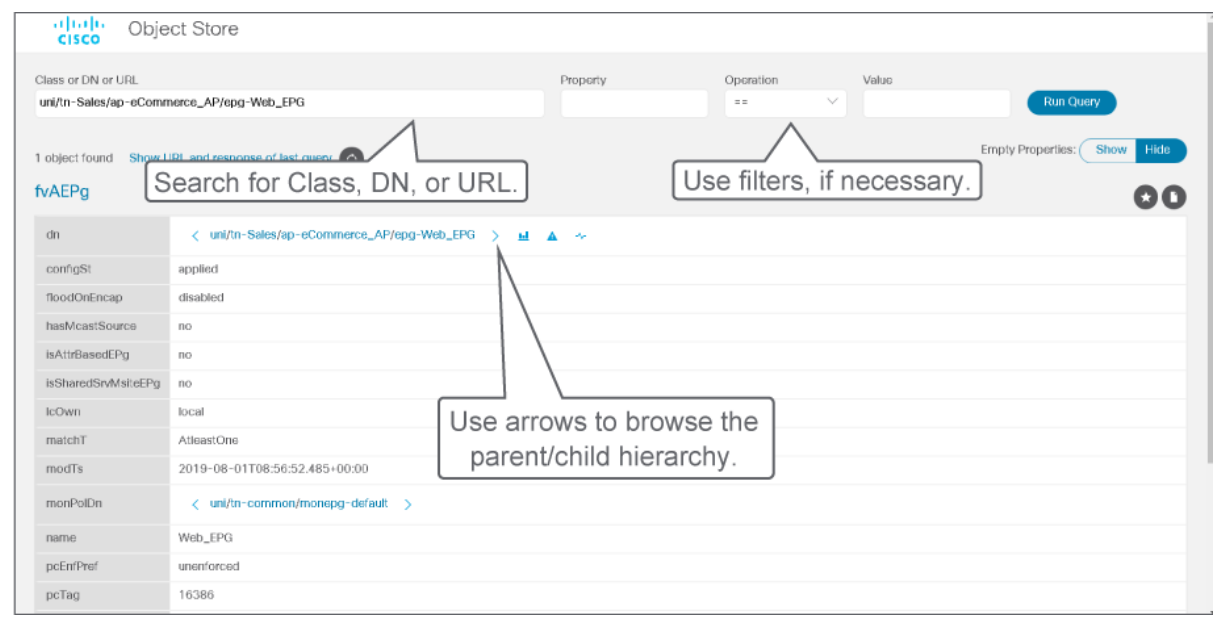
To query for a particular class, enter the class name in the Class or DN field and click Run Query. Object Store Browser sends a configResolveClass method to Cisco APIC and the requested MO is displayed in a tabular format. Use the less than (<) and greater than (>) buttons to retrieve the parent and child class of the displayed MO.
To query for a particular DN, enter the DN in the Class or DN field and click Run Query. Object Store Browser sends a configResolveDn method to the Cisco APIC.
Moquery
Moquery is a CLI utility that allows querying of the MIT from the command line. It is also known as the command-line cousin to Object Store Browser.





LEAVE A COMMENT
Please login here to comment.