EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USWhy Digital Transformation Needed ??
In today’s hybrid-work environment, organizations must modernize their security approach to protect users, applications, and devices across any network. Traditional perimeter-based models are no longer sufficient against modern, sophisticated cyber threats and data‑loss risks.
Zscaler addresses this challenge through its Zero Trust Architecture, delivered via the world’s largest security cloud. By validating identity and context for every connection—not the network location—Zscaler secures users, workloads, and IoT/OT devices. This cloud‑native model simplifies operations, enhances user experience, reduces attack surfaces, and accelerates digital transformation by ensuring fast, safe, and seamless access from anywhere.
Zscaler for Users provides three key solutions in order to provide fast, secure, and reliable access to internet, SaaS, and private apps:
- Secure Internet & SaaS Access
- Secure Private App Access
- Digital Experience Monitoring
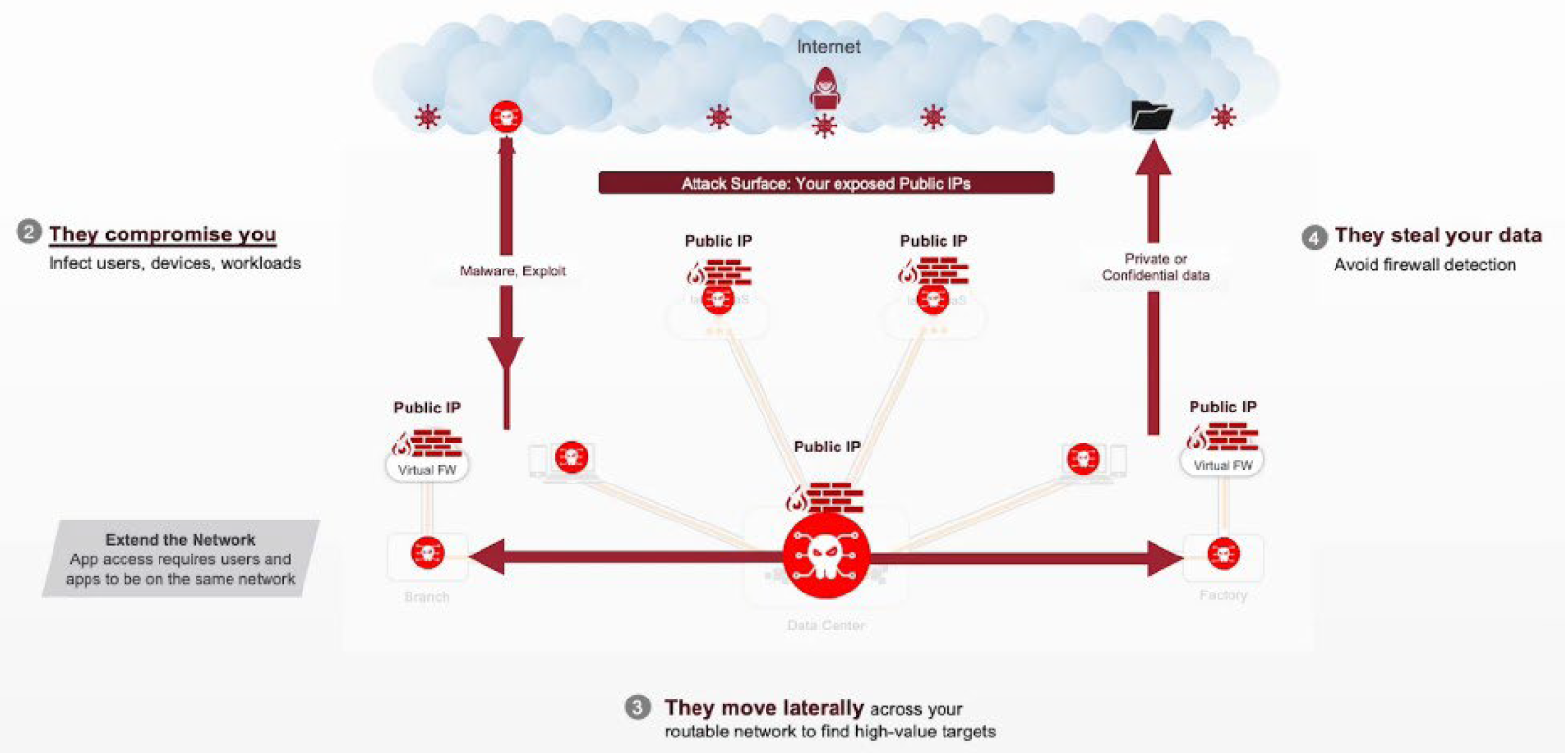
Traditional network architectures rely on extending a routable corporate network (“golden line”) from the data center to branches, remote users (via VPN), and now to public cloud workloads. This approach creates major security risks because:
- Virtual firewalls are discoverable and attackable, making them vulnerable to threats such as DDoS.
- One compromised VPN credential can give attackers full network access, enabling lateral movement to critical systems and eventual data exfiltration.
This outdated design has contributed to several major breaches—such as the Colonial Pipeline attack—highlighting why a modern Zero Trust model like Zscaler’s is required.
What is Zero Trust?
Zero Trust focuses on connecting a user only to the specific application they need—without ever placing them on the network. In a traditional VPN or firewall model, once a user authenticates, they gain broad network visibility and can move laterally, scan systems, and potentially access or exfiltrate sensitive data.
Using the analogy of visiting a building:
-
Legacy (VPN/Firewall) Model:
You can see the entire building (data center, AWS, Azure), enter it once authenticated, wander freely, discover sensitive areas, and leave with data. This mirrors how VPNs inherently grant full network access, enabling lateral movement and risk of data theft.
Solution:
Zero Trust Exchange (Zscaler) Model
You cannot see the building at all. Instead, you are securely escorted directly to only the specific application you’re authorized to access, without network visibility. You're also inspected for threats before entry and exit, preventing data exfiltration.
This user-to-application approach—eliminating network access and visibility—is the core of Zscaler’s Zero Trust Architecture.
The analogy compares public exposure of a phone number to exposing applications or firewalls on the open internet. When something is publicly reachable, anyone—including attackers—can find, spam, or attack it (like DDoS on a public firewall).
With a Zero Trust Exchange, the application’s “number” is unpublished. Only explicitly authorized users can connect. The Zero Trust Exchange first verifies the caller’s identity, and only then establishes a secure, direct connection between the user and the application. This prevents unwanted discovery, attacks, and unauthorized access—illustrating the core value of Zscaler’s Zero Trust model.
how the Zero Trust Exchange architecture works:
-
Connection Termination and Identity Verification
Every connection—whether from a user, workload, or IoT/OT device—is first terminated at the Zscaler platform. At that point, Zscaler evaluates the connection by asking: Who is the entity? Where is it coming from? Where is it trying to go? What is the context of the request? -
Risk Assessment and Traffic Inspection
Next, Zscaler analyzes the traffic for risk. This includes full SSL inspection—critical since most internet traffic is encrypted—and checks for data loss. For example, if a user attempts to access a sensitive internal application, Zscaler ensures they can’t download confidential files or transfer intellectual property. -
Policy Enforcement and Access Control
Finally, Zscaler applies the appropriate security policy. Depending on the risk level, the user may be allowed access, denied access, or routed through Cloud Browser Isolation. In isolation mode, only pixels are streamed to the user, preventing any direct interaction with or download from the application. Once policy is enforced, a secure connection is established to the required internet or private application.




LEAVE A COMMENT
Please login here to comment.