EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USIntegrating Traditional Network with ACI
The leaf-spine and Layer 3-based nature of the Cisco ACI fabric defines that non-ACI nodes (servers, routers, firewalls, load balancers, switches, and so on) are connected at the leaf level only.
The classic network segments may implement the following features and specifics:
- Multiple endpoints are connected via a single leaf port.
- Endpoints that are not directly connected to the Cisco ACI fabric.
- Port channels and virtual port channel (vPCs) aggregating links and switches are used to omit the limitations of STP.
- Interaction with STP domains and potential Layer 2 loops due to misconfiguration or misconnectivity in the switched topology.
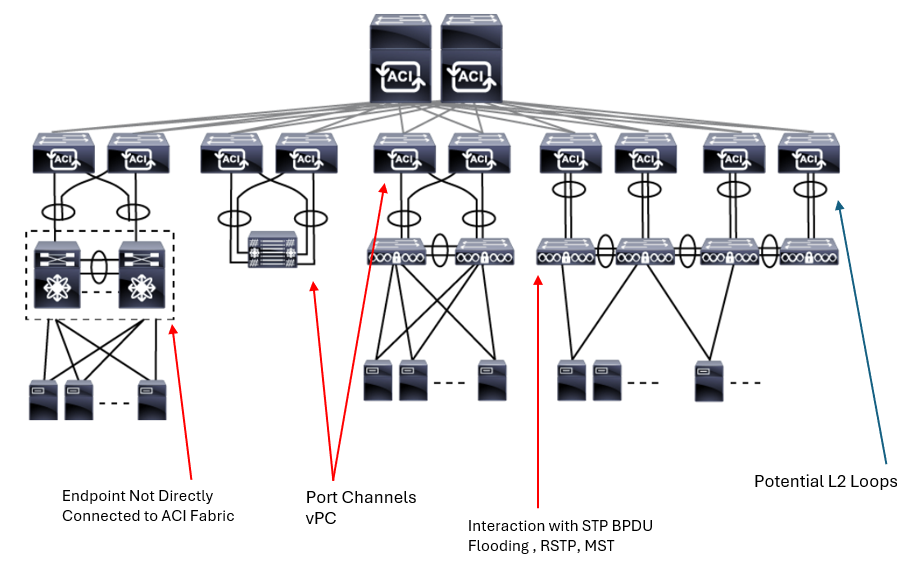
Nondirectly Connected Endpoints
Endpoints that are not directly connected to the Cisco ACI fabric are still learned in the same way as other endpoints. But it traverses through the external Layer 2 network first and not all the traffic from them may hit the Cisco ACI fabric.
Cisco ACI can optimize traffic by preventing flooding for ARP requests and/or Layer 2 Unknown Unicast packets. This optimization is called Spine-Proxy, which allows the packet to be sent only to the interface connected to the destination such as the target IP of the ARP request. However, for endpoints that are not directly connected to the Cisco ACI leaf switches, this optimization may need to be turned off so that the Cisco ACI fabric floods those packets like a classical Ethernet network does.
The issues with Spine-Proxy and external Layer 2 network may arise upon switched topology changes, for example, a link from one switch that is connected to the Cisco ACI fabric fails. The switched topology converges around that using links to another Cisco ACI leaf switch. At the same time, the endpoints learned through the link that failed are cleared from both the endpoint table on the leaf and the COOP database on spine switches. If other endpoints that are in the same subnet as those cleared endpoints try to send traffic to them through the Cisco ACI fabric, it may fail if the Cisco ACI fabric has not yet re-learned the cleared endpoints on the new converged interface.
The packets may be dropped because the other endpoints may have the ARP cache for the cleared endpoint and send unicast bridged traffic to them without broadcasting ARP requests first. This traffic is Layer 2 Unknown Unicast traffic for the Cisco ACI fabric, and it is dropped if the cleared endpoints are not learned yet on the Cisco ACI fabric and Spine-Proxy is used for Layer 2 Unknown Unicast. If flood is used, the Cisco ACI fabric can flood the traffic through leaf, spine, and external Layer 2 network without any problems.
Therefore, the BD Cisco ACI configuration for such segments is recommended to be adjusted with the following:
- Layer 2 unknown unicast flooding enabled.
- ARP flooding enabled.
Port Channels & vPCs
A vPC on the Cisco ACI is implemented between two leaf switches designated as vPC peer switches—one being primary and one being secondary joined into a vPC domain. There is a couple of specifics with a Cisco ACI implementation when compared to a non-ACI implementation.
There are no direct dedicated peer and peer-keepalive links that are used between the leaf switches that are part of the vPC domain. Instead the Cisco ACI fabric is used for the purpose and vPC pair gets additional TEP virtual IP address. The vPC configuration is implemented in the form of policies. The vPC domain and vPC protection group policies create the vPC domain, vPC interface policy group is used to apply configuration at the interface level.
Interaction with STP Domains
Although the Cisco ACI fabric does not participate in STP domain with other external Layer 2 switches, it still forwards the STP BDPU from one external switch to another through so that the external switches can maintain their loop free topology even through the overlay network that is provided by the Cisco ACI fabric.
Cisco ACI Leaf VLAN and VXLAN Usage
Endpoints connected to Cisco ACI leaf switches continue to use and consume VLANs the same way they used them—traffic is either sent via native, that is, untagged or 802.1Q tagged VLANs. Cisco ACI leaf switches then perform mapping of the endpoint VLANs into fabric VXLANs for the traffic to be sent across the fabric.
The internal mapping process uses several VLAN and VXLAN identifiers that are assigned to different Cisco ACI constructs and used to forward different types of traffic.
Access encapsulation VLAN (ACC_ENCAP) is the VLAN that is used for the traffic on the wire between endpoint (or switch, router, firewall, port) and leaf port. In the Cisco ACI configuration, this VLAN is configured as part of a selected VLAN pool and enabled for the selected EPG for the port where the endpoint is connected.
BD_VLAN is a leaf locally significant VLAN assigned to each configured BD. BD_VLAN is translated into VXLAN ID that is the same on every leaf switch for the same BD. On top of bridging traffic in the BD, most of the packets of the traffic that may need to be flooded in a Layer 2 domain (for example, broadcast, multicast, and unknown unicast) are sent to the fabric using multicast through the BD VXLAN.
FD_VLAN is a leaf locally significant VLAN assigned to the individual configured access encap VLAN in an EPG. A BD will typically have multiple access encap VLANs each with its own FD_VLAN ID, which are children to BD_VLAN. FD_VLAN is assigned a VXLAN ID that must be the same across all leaf switches where that particular access encap VLAN for the EPG should be present.
For some flood traffic, the FD_VLAN (that is, its VXLAN ID) is used to forward the traffic instead of VLXLAN ID of the BD_VLAN.
The presented Cisco ACI fabric is configured with two EPGs each encompassing its own access encapsulation VLAN:
- EPG1 that is used for endpoints belonging to access encap VLAN 2110
- EPG2 that is used for endpoints belonging to access encap VLAN 2111
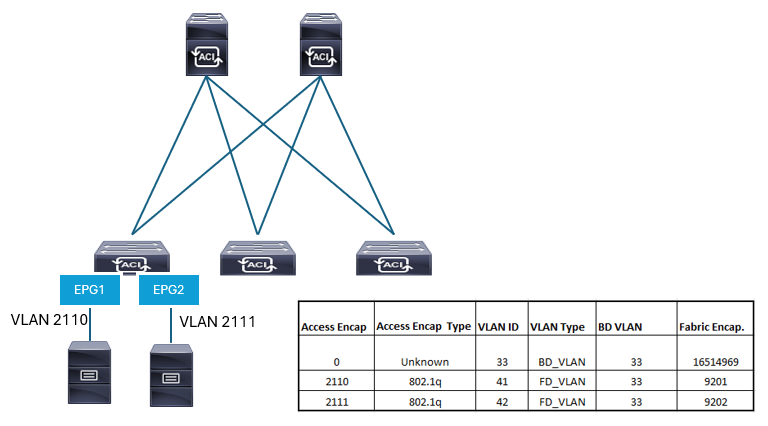
BD is assigned the locally significant BD_VLAN ID of 33 and fabric encapsulation VXLAN ID 16514969. Since BD_VLAN is not used at any interface, the access type is unknown (that is, the BD_VLAN is not used as access encapsulation VLAN).
The access encapsulation VLANs are mapped to local FD_VLANs and fabric-wide VXLANs:
- VLAN 2110 is mapped to FD_VLAN 41 and VXLAN ID 9201
- VLAN 2111 is mapped to FD_VLAN 42 and VXLAN ID 9202.
Both belong to the same BD since they are part of the same Layer 2 domain.





LEAVE A COMMENT
Please login here to comment.