EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSecurity of Internet Breakouts
Previously, a centralized internet breakout model was routing outbound traffic through the company's centralized gateways which implemented additional security measures. The centralized gateways also provided proxies, antivirus features, and firewalls. However, the volume of internet bound traffic is exceeding the capacity of those centralized internet circuits and creating a bottleneck.
In contrast, the local breakouts allow each remote office and branch to possess its access point for connecting to the internet. Also, they require having the same historical protections offered previously, such as firewalls, Application Traffic Policies (ATP), DLP, IPS, and sandboxing. Taking the existing corporate security stack and reproducing it on every breakout is too cost-ineffective challenging to manage, update, and synchronize. Also, you cannot use NGFWs for native cloud application support. You can overload NGFWs by the number of high-duration connections that the applications require to function. As such, they end up throttling the applications and diminishing user productivity in the process. The same goes for native support for Secure Sockets Layer (SSL) traffic, as they require third-party solutions to properly perform SSL inspection on the software level because they don't do it through chips). In this case, it dramatically decreases the system's overall performance and disturbs user workflow.
Because classic firewalls and appliances cannot meet a local internet breakout's security standard, security for them must move to the cloud.
This approach can give you several advantages over traditional security stacks, such as:
- Higher security and speed for users: By using cloud-based security and direct routes from branches to the internet you gain the best of both worlds—the ability for users to properly utilize all the popular cloud applications without any compromises on speed and security.
- Location-agnostic protection: Whether you connect from the home network, a public network at a restaurant, or one of the corporate offices, as long as you do it through the same cloud security, the session will remain equally safe no matter where you are.
- Ease of IT: Cloud-based security provides centralized access to all traffic control functions. Also, you can establish new policies, services, and application priorities through a single pane of glass.
- Cost reduction: Utilizing a centralized security solution, you can deploy the local internet breakouts necessary to turn away any excess outgoing traffic from the MPLS infrastructure. Also, you can adequately monitor and manage all of it without buying and deploying multiple identical security solutions for every breakout. All this can lead to significant long-term savings.
Cisco SASE Use Case—Thin Branch
In this use case, you are located on-premises, and the secure edge is your colocation, branch office, campus, and maybe a home office that has a hardware device protecting the home network.
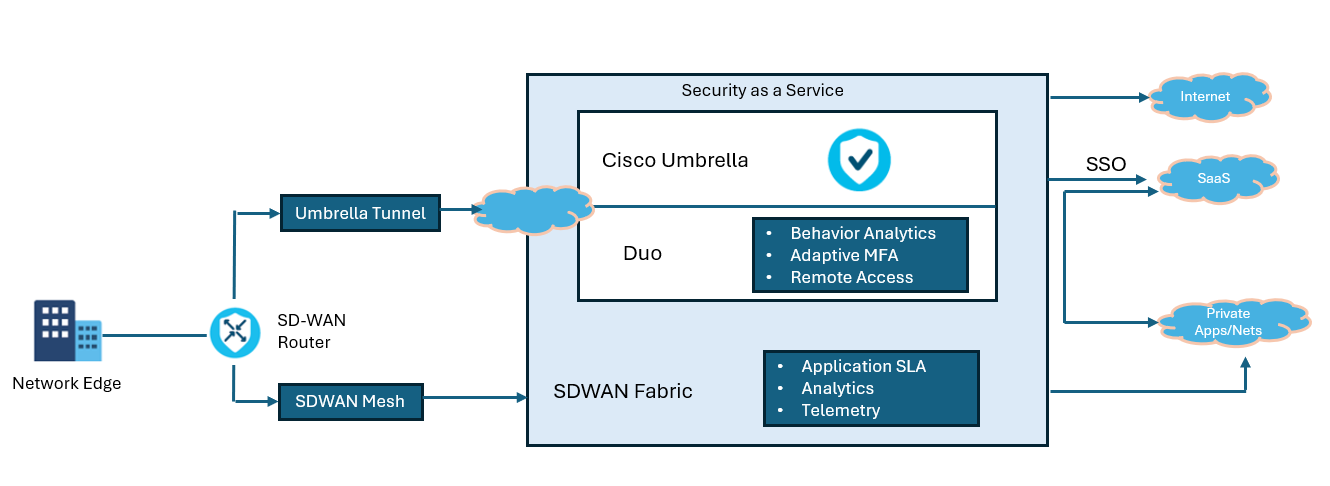
You can use the Cisco SD-WAN fabric as a crucial connection component and benefit from dynamic path selection, safe transport, application-aware routing, and other built-in Cisco SD-WAN features.
Cisco SD-WAN—particularly the vManage component—supports integration with Cisco Umbrella secure service. You can configure a dedicated template on vManage to point your traffic to a SIG (Umbrella) interface. This template has a policy consisting of Umbrella’s unique DNS re-direct rules on a per VPN or all VPN basis. Your traffic can reach the network’s local resources on internally hosted domains that rely on local servers. Other traffic points to the Cisco Umbrella SIG interface where Umbrella will apply its security services.
if you need to deploy 100 or 1000 branches, you do not want to manage the same parameter security stack across every one of those branches. You can move most of that security stack into the cloud and provide a common policy for all your branches. Also, you will need to set up a tunnel for traffic to go through this security stack in the cloud. This is why SASE exists and why security as a service is so popular.





LEAVE A COMMENT
Please login here to comment.