EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USCisco ACI Access Policies
Access policies configure external-facing interfaces that connect to devices such as hypervisors, hosts, network attached storage, routers, or FEX interfaces. Access policies enable the configuration of port channels and virtual port channels, protocols such as Link Layer Discovery Protocol (LLDP), Cisco Discovery Protocol (CDP), or Link Aggregation Control Protocol (LACP), and features such as statistics gathering, monitoring, and diagnostics.
-
Access policies:
-
Mandatory for attaching any endpoints to leaf switches
-
Identify the access interfaces on Cisco ACI switches
-
Authorize encapsulation resources (VLAN)
-
-
Fabric policies define fabric functions, such as:
-
Network Time Protocol (NTP), Domain Name Server (DNS), and Multiprotocol Border Gateway Protocol (MP-BGP) route reflector on spine switches
-
Access policies are grouped into the following categories:
-
Pools: Specify VLAN and multicast address pools.
-
Interface profiles: Specify which access interfaces to configure and the interface configuration policy.
-
Switch profiles: Specify which switches to configure and the switch configuration policy.
-
Module profiles: Specify which leaf module to configure. But as of release 4.1, there is no leaf model that has more than one module. Hence this profile is typically never used.
-
Global policies: Enable the configuration of DHCP, QoS, and Attachable Access Entity Profile (AAEP).
-
Physical and external domains: Define a domain that bundles a set of interfaces (AAEP) and encapsulations (VLAN pool) to allow other components.
-
Monitoring and troubleshooting policies: Specify what to monitor, the thresholds, how to handle faults and logs, and how to perform diagnostics related to external facing interfaces.
Interface Policies, Switch Policies, and Profiles
The configuration of access ports in Cisco ACI fabric requires the use of Interface Policies and Switch Policies.
With interface policies, you can perform these actions:
-
Create protocol policies to configure interface protocols and parameters.
-
Choose a port connection type, such as vPC with an interface policy group.
-
Group ports with an interface profile.
With switch policies, you can perform these actions:
-
Create or modify protocol policies at switch level with a Switch Policy.
-
Group one or more leaf switches as one switch group with Switch Profile Policy.
-
Associate a switch profile with an interface profile.
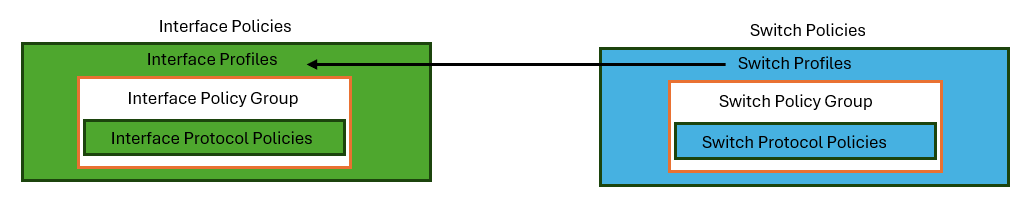
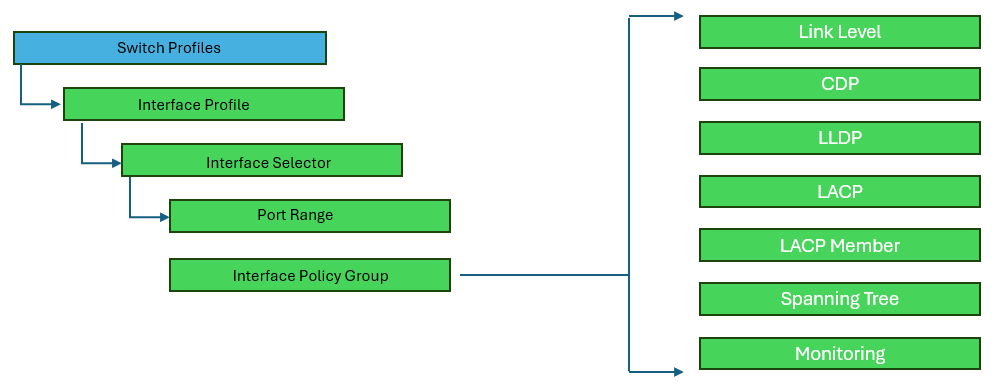
Interface Protocol Policies
Interface policies dictate interface behavior, and are later tied to interface policy groups that bundles sets of interface policies as a template.
Examples of the protocols that can be configured are:
-
Link-Level
-
LLDP
-
Cisco Discovery Protocol
-
LACP
-
NetFlow
-
Control Plane Policing (CoPP)
For each policy, users can create one policy per interface, or create a reusable policy as a template and apply it to multiple interfaces. For example, users can create two policies, LLDP_ENABLE and LLDP_DISABLE, and use them for all interfaces.
Interface Policy Groups
Interface policy groups are templates that dictate interface level configurations via Interface Protocol Policies and are associated to an AAEP. Interface Policy Groups are also reusable objects for ports that will require the same port configuration. There are three basic types of interface policy groups depending on the link type: Leaf Access port, Port Channel, and vPC.
Policy group gathers interface policies into a bundle:
-
Cisco Discovery Protocol, LLDP, LACP ...
Policy group is linked to:
-
Interface selector (specifies to which interface block the policies apply)
-
An AAEP (Attachable Access Entity Profile) to be bundled under a domain so that a domain can provide a set of interfaces and encapsulation resources
There are three basic types of policy groups:
-
Access port
-
Port Channel
-
vPC
A set of interface policy groups should be created for each type of similar devices that are connected. For example, there can be a set of interface policy groups for all VMware ESXi servers that are connected via 10-Gigabit Ethernet vPCs, and a different set of interface policy groups for all bare metal servers running 1-Gigabit Ethernet with Cisco Discovery Protocol disabled.
Interface Profiles & Switch Profile
Interface profiles contain blocks of ports (interface selectors) and are also tied to the interface policy groups.
Within an interface profile, you use the interface selector to choose a port or a port range and bind the ports with an interface policy group. Switch profiles allow you to group one or more leaf switches as one object with the use of switch selector. You need to associate a switch profile with an interface profile. In this way, the ports on the destination leaf switch will be activated with the properties and protocols defined in the Interface Policy Group.
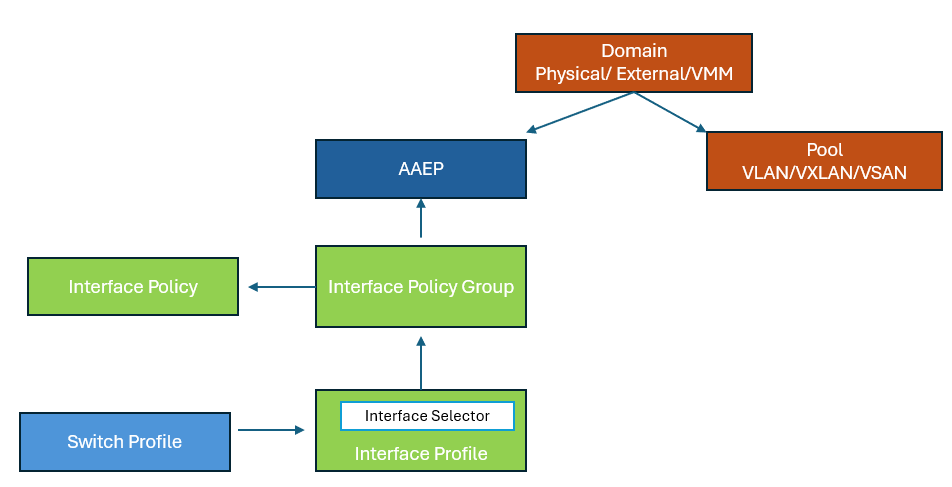
Domains and Attachable Access Entity Profiles
A physical domain profile stores the physical resources (ports and port channels) and encapsulation resources (VLAN/VXLAN) that should be used for endpoint group connections to the fabric.
AAEP itself does not directly connect to other components.
You can configure the following domain types:
-
VMM domain profiles: required for virtual machine hypervisor integration.
-
Physical domain profiles: typically used for bare metal server attachment and management access.
-
Bridged outside network domain profiles: typically used to connect a bridged external network trunk switch to a leaf switch in the Cisco ACI fabric.
-
Routed outside network domain profiles: used to connect a router to a leaf switch in the Cisco ACI fabric.
An AAEP (or AEP) is a component that bundles group of interfaces through Interface Policy Groups, which contain multiple interfaces that share same port level policies such as LLDP. An AAEP is attached to a domain so that a domain can provide a group of interfaces (via AAEP) and VLANs (via VLAN pool) to the logical resources such as EPG, L3OUT. An AAEP can be attached to more than one domain. AAEPs are configured under global policies.
Access Policies Relationship
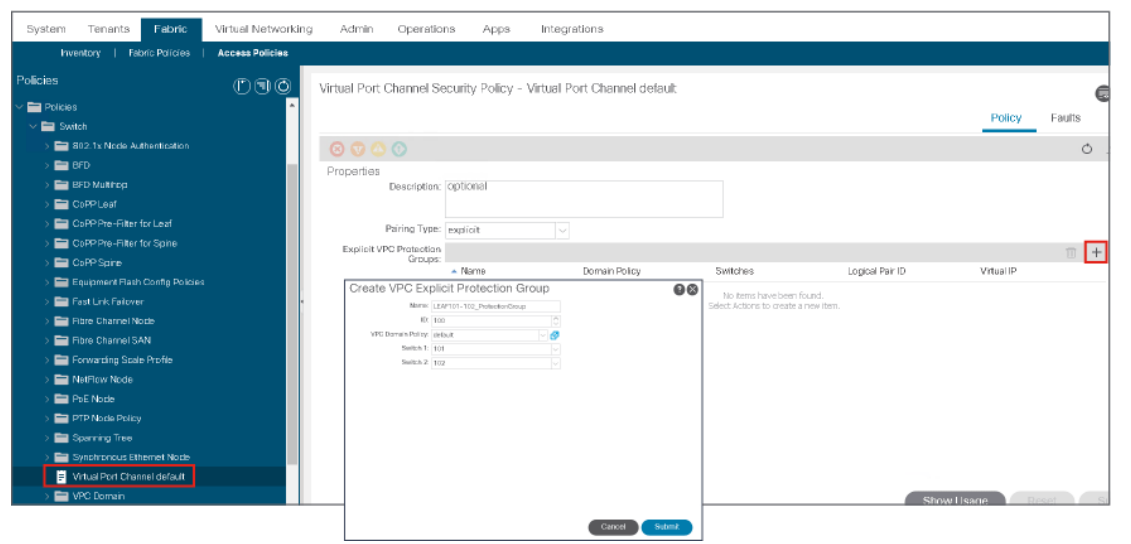
vPC in Cisco ACI Fabric
A vPC domain is associated with a vPC security policy. The vPC security policy defines the leaf switches that belong to the vPC domain. To create a vPC domain, navigate to Fabric > Access Policies > Policies > Switch and choose Virtual Port Channel default. Click the plus sign (+) in the Explicit vPC Protection Groups table to add a group.
Adding two leaf switches to a vPC security policy:
Use of vPC in Cisco ACI FEX Topologies
FEX connectivity has been designed to provide cost-effective 1-Gigabit Ethernet and 10-Gigabit Ethernet server access connectivity. It is supported by the Cisco Nexus 9300 and 9500 Series systems. Cisco Nexus 9500 Series Switches support a maximum of 32 FEX modules.
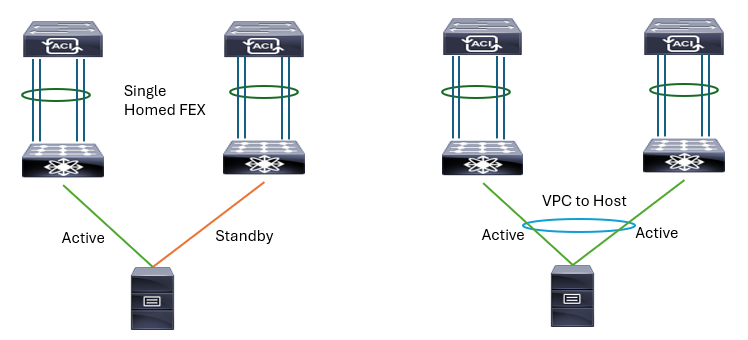
Cisco ACI supports the following FEX topologies:
-
A single-homed FEX topology
-
vPC to the host interfaces (HIF)
Cisco ACI Access Policies Design Suggestion
Defining a naming convention for the Cisco ACI objects and policies is a recommended practice. It provides the benefit of easier implementation of Cisco ACI configuration, monitoring, and management.
Naming convention and design of access policies suggestion:
-
Rule 1: Creates one switch profile for each node (LEAF101_SWP, LEAF102_SWP) and one switch profile for each vPC pair (LEAF101-102_SWP)
-
Rule 2: Create one interface profile for each switch profile (LEAF101_IFP, LEAF102_IFP and LEAFS101-102_IFP)
-
Rule 3: Associate each switch profile to each interface profile one by one (LEAF101_SWP = LEAF101_IFP...)
-
Rule 4: Add an interface selector under a prepared interface profile instead of creating a new one for every interface selector.
How to Configure Access Policies—Sample Use Case
Imagine the following use case: You have a server connected to your ACI fabric. Your server has 2 NICs, and these adapters are configured in an LACP port channel. The server is connected on port 1/9, ACI leaf nodes 101 and 102. To communicate, the server must have an external VLAN 1501 allowed on these ports.
Topology:

Switch Profile
First, using a switch profile, create a policy in Cisco ACI that defines which switches need to be used. Define which switches are part of the switch profile through a switch selector.
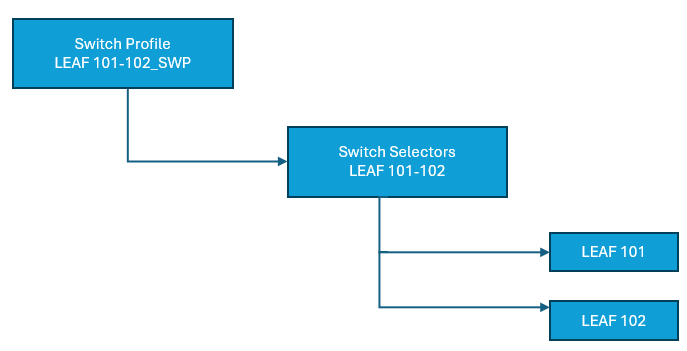
Deploy a naming scheme that can easily be followed. The name scheme can consist of LEAF{node-id}_SWP. As an example LEAF101_SWP is for a switch profile containing node-101; LEAF101-102_SWP is for a switch profile containing switches 101–102 which are part of a vPC domain.
Interface Profile
Once you define which switches need configuration, you can define the ports on these switches that require the configuration, by creating an interface profile, which consists of 1 or more access port selectors.
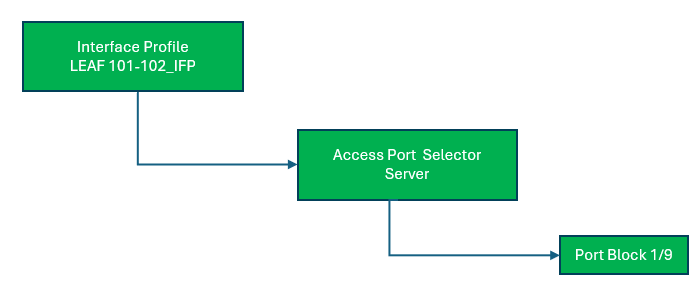
The name scheme of an interface profile can consist of LEAF{node-id}_IFP. For example, LEAF101_IFP is for a profile that is used for a non-vpc interface on switch 101 and it would map directly to the LEAF101_SWP switch profile. Another example would be LEAF101-102_IFP for a profile that is used for a vPC interface on switches 101 and 102 and it would map directly to the LEAF101-102_SWP switch profile.





LEAVE A COMMENT
Please login here to comment.