EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USCisco SD-WAN with Dedicated Security
Cisco SD-WAN offers integrated, on-box security services, such as an application-aware enterprise firewall, an intrusion detection and prevention system, advanced malware protection, and Cisco URL Filtering. Hardware platforms can limit the integrated security services and their performance.
When the required throughput with security enabled exceeds the capabilities of the Cisco SD-WAN Edge routers, or if there is a requirement for the additional features, organizations can do one of these two things:
-
Upgrade the WAN Edge routers to meet requirements.
-
Deploy dedicated security services.
Cisco SD-WAN can integrate dedicated security services by using service insertion or service chaining. Service chaining enables administrators to deploy dedicated security services, either on-premises or in the cloud, with the required performance levels. Cisco SD-WAN then advertises these services into the Cisco SD-WAN fabric, so the network is aware of their existence. Then, administrators can configure control or data policies to force certain traffic flows and their rerouting process through those services for inspection.
Service Chaining
Service chaining allows rerouting data traffic through one or more services, such as firewall, load balancer, or intrusion detection and prevention devices. Services can be deployed in one location or distributed across multiple locations for redundancy. They may also be internal to the corporate network, external, or cloud-based.
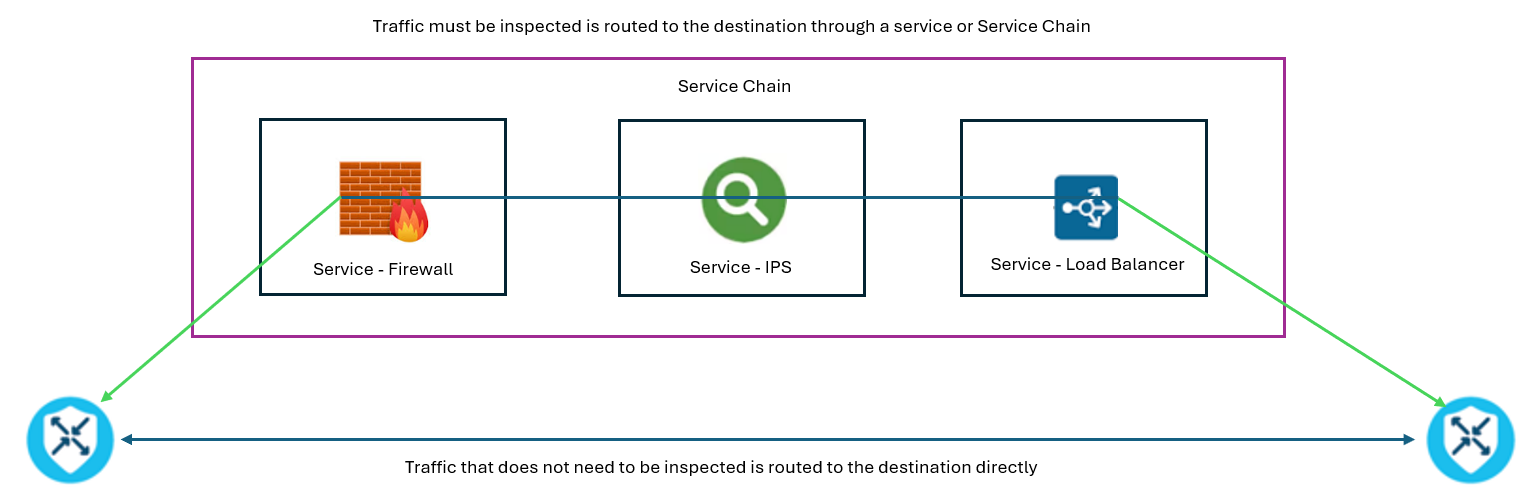
With service chaining in Cisco SD-WAN networks, the network advertises the service, such as a firewall or a load balancer, and one or more services route traffic by using policies.
Here are a few of the reasons to route traffic through a service or a service chain:
-
Traffic from one region of a network must pass through a service, such as a firewall, or through a chain of services to ensure that the data has not been tampered with.
-
Traffic between VPNs must traverse through a service, such as a firewall, or through a chain of services. For example, in an organization, traffic between departments should go through a firewall, while traffic within the department should be routed directly.
-
Certain traffic flows should pass through a service, such as an intrusion prevention system (IPS). For example, in a financial institution, an IPS solution must secure any traffic flow to a system that stores credit card data.
Benefits of Service Chaining
Below are some benefits of Service Chaining
- Automation
- Flexibility
- Scalability
- Cost Efficiency
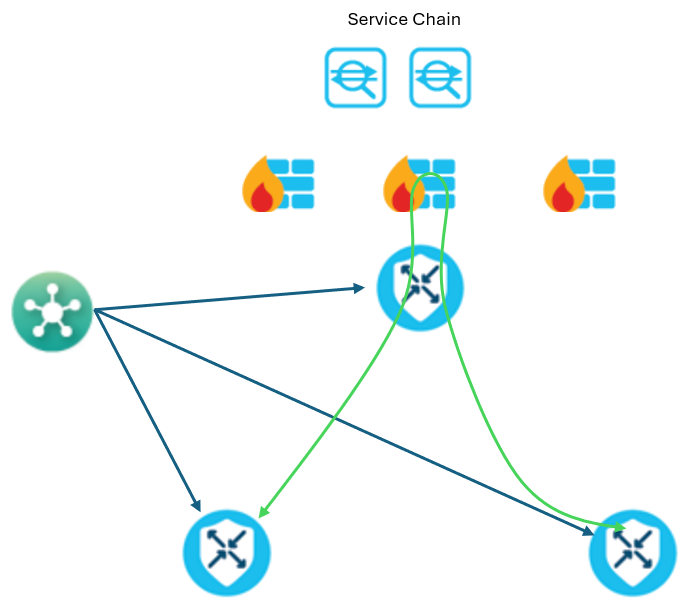
Service chaining also enables increased scalability in the sense that organizations can deploy the services on-demand, as and when required. The administrator can decrease the number of services when they are not required. The ability to deploy and activate the services on-demand also improves the cost-effectiveness of network operations.
Routing Inter-Site Traffic Through a Service
To deploy service chaining in such a scenario, the administrator must perform multiple tasks. The tasks include deploying the firewall and configuring routing and security policies on the firewall. The administrator must deploy the firewall and configure and advertise the service into the Cisco SD-WAN fabric.





LEAVE A COMMENT
Please login here to comment.